Margaretta D’Arcy found herself jailed in January 2014 on the back of a protest she mounted at Shannon Airport in 2012. What was she protesting about? US troop aircraft using Shannon as a stopover on their journey to the warzones of Iraq and Afghanistan among other things. D’Arcy is a rare stalewart against the steady erosion of Ireland’s vague understanding of its declared neutrality.
The New Battlefields
Unfortunately, in our increasingly connected technological world she was fighting the right battle on the wrong battlefield. Troops landing on the ground have increasingly been replaced by drones in the sky commanded by the video-game generation from air-conditioned facilities in the comfort of their own country. This arms-length war is conducted in part through the use of the numerous transatlantic cables that crisscross the seabed, many of which land in Ireland before continuing on their journey to the United Kingdom and the rest of Europe. As to the number of deaths that can be attributed to commands that were routed through cables that land in Ireland we can only speculate, but as the Galway Alliance Against War statement asserted on the occasion of the conviction of Margaretta D’Arcy:
“By allowing the US Military to use Irish airspace and Shannon airport to wage these wars we have become a willing accessory to mass murder. We have blood on our hands…”.
By logical extension, by allowing the command and control systems to communicate across infrastructure that connects through Ireland we continue to support these military operations in opposition to the basic principles of our perceived neutrality.
Not a New Problem
The first transatlantic communications cable was laid between Newfoundland and Ireland in 1866. One of the first communications transmitted across that cable was from Queen Victoria to then President James Buchanan:
“A treaty of peace has been signed between Austria and Prussia”.
The cost of transmitting messages across the transatlantic cable was prohibitive, limiting its usefulness to the affluent, wealthy organisations and of course governments.
The strategic value of the cable was further emphasised in the explicit agreement for the UK to retain the right to determine control of it after the establishment of the Irish Free State in 1922.
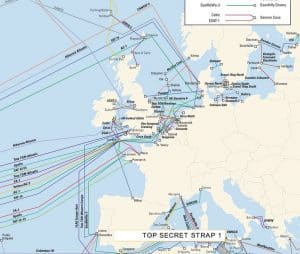
We might like to think that in the intervening years Ireland had grown to the point where it exercises control over the cables that land here. In 2014 Edward Snowden’s WikiLeaks revealed the degree to which the influence of Britain’s security services and General Communications Headquarters (GCHQ) has hardly diminished. The Irish Government has failed to address this issue.
The actual number of cables connecting the US to its closest strategic partner, the UK, is startlingly few: discounting cables that form loops, there are seven. Eliminating those that connect through the rest of Europe, such as France or Denmark, the number reduces to four. Of those four three are routed through Ireland.
The relevance of these connections can be easily understood when one looks at what traffic is going through these cables.
Nippers and Slippers
The United States Military operates a number of private networks, that are not connected to the public Internet. They have fantastic names such as JWICS (Joint Worldwide Intelligence Communications System), Secure/Secret Internet Protocol Router Network (SPIRNet or slipper), Non-classified Internet Protocol Router Network (NIPRNet or nipper) and National Security Agency Network (NSANet). These networks all fall under the umbrella of the Defence Information System Network (DISN), a worldwide system that connects US interests. These interests include in this case: command and control centres, intelligence agencies, embassies all the way out to Joint Task Force/Coalition Task Force troops on the ground. Included in the numerous global points to which slipper and nipper connect is the US Embassy in Dublin.
You may wonder how the US Military managed to get access to all of the required jurisdictions to lay a private network of cables across the globe. The answer, unsurprisingly, is that they didn’t. Instead they purchase services from private infrastructure companies which have already laid the required cables. Companies like those which land in the likes of Dublin, Cork or Sligo.
These networks are designed to be ‘Airgapped’ i.e. they are intended to operate physically isolated from each other and physically separated from the public Internet. According to protocol, any device connected to slipper for example, is supposed to automatically fall under the control of the slipper protocols and by extension the DISN protocols. The allegations against Hillary Clinton during the 2016 elections specifically relating to the handling of secret information are based on her having access to information from slipper but using an insecure device.
Slipper, nipper, JWICS and the rest leverage private infrastructure but are supposedly separated from the rest of the Internet, but there is some evidence to suggest that this isn’t entirely the case.
Marines Building Tunnels
In 2002, as the US was starting to land troops on their way to Afghanistan and the Middle East, in Shannon Airport, a resourceful team of Marines developed a new mechanism for accessing the nipper and slipper networks. In consultation with a private contractor, the Marines built a ‘tunnel’ that allowed a secure channel to be established to slipper from a lower classified network – lower classified networks include nipper of course but also the public internet. The tunnels are now understood to be Virtual Private Networks (VPNs) that are in daily use by private industry. The implication of this ostensibly innocuous development is that the military themselves have transcended the security of their own private network using what is now off-the-shelf technology.
Did You Lose Control of the Drones?
At the intersection of the video-games universe and the US military is Creech Air Force Base, just outside Las Vegas, Nevada. From there Air Force pilots remotely control the surveillance, information-gathering and ‘targeted killing’ Drone operations. Among the many different forms of information communicated to and from Creech is target-designation information – focusing on who is to be killed. This information is communicated via our now familiar slipper network.
On 9 September 2016 the network at Creech crashed, affecting ‘critical services’. Services fell back to less powerful devices which temporarily stabilised operations but it was stated at the time that there was no backup if that solution failed under load. The US Air Force has been somewhat tight-lipped regarding the root cause of the outage, whether it was a crash or a cyber attack but what is not disputed is that one of the critical services that was affected, however briefly, was control of Drones – Drones with weapons.
It is unclear whether what followed was a direct result of the crash or unrelated. Within weeks of the crash, a series of Drone related airstrikes went badly wrong. The litany of errors included:
- September 17: 62 Syrian Soldiers accidentally killed by US airstrike during a ceasefire
- September 18: 15 civilians killed in Afghanistan by Drone strike
- September 18: 22 Somali soldiers killed by US Drone strike
So far, no explanation for these failures has been forthcoming, but on October 7 2016 the Air Force announced that Creech would be subject to a surprise cyber security inspection.
Surprise Security Checks

The rest of the page highlights the imperatives that personnel should be aware of including not sharing secret information via, amongst other things, social media.
Other areas that personnel, including the Drone ‘pilots’, were encouraged to consider include:
“Exercising your mental skills by memorizing login credentials is also vital. Stay away from writing them down”.
And perhaps even more alarming:
“Continue to be wary of phishing attempts; each and every day people fall victim to cyber hacks conducted via adversary phishing tactics, techniques and procedures”.
In summary: don’t share secrets on Facebook, try to remember your password, presumably including the codes that allow Drones to fire on targets, and finally don’t trust everything you read in your email.
But if slipper is ‘Airgapped’ as stated, how is the system vulnerable to leaks via social networks?
Of course Cyber Command came into existence as a result of a previous hack – Operation Buckshot Yankee – where a USB drive was apparently left in the parking lot of a Defence Department facility. That USB was subsequently attached to a laptop computer releasing malicious code dubbed agent.btz on the military networks taking 14 months to eradicate.
Can Ireland Be Neutral?
Putting all of the pieces together, we know that private networks are utilised by the US Military to connect its various operations, some diplomatic and some offensive military operations. We know that GCHQ in the UK has maintained access to this infrastructure, including transatlantic cables that terminate or land in Ireland.
Questions should be raised at Government level to determine what if anything has been done to ensure that military traffic, particularly that used in offensive operations, does not pass through Irish infrastructure. Is this challenge to our neutrality deliberate or a blind spot as a result of ignorance of the technology?
Afterthought – The Future of Drones

The US and its military are facing a crisis concerning its Drones. Pilots are leaving in significant numbers, citing Post Traumatic Stress Disorder (PTSD). While we may struggle to sympathise with the pilots who leave their comfortable facility in Nevada to travel home to their well-appointed houses in Las Vegas having wiped innocent people from existence, we should be deeply concerned by the proposals to deal with the problem. The US Air Force is attempting to leverage Artificial Intelligence technologies to allow Drones to designate their own targets. In effect they are proposing the development of an autonomous fleet of armed robots. It all evokes the ‘Hunter Killer’ in the Terminator series – a flying, autonomous, armed military robot.
Stephen Hawking has been quite clear on his concerns relating to Artificial Intelligence, which I’ll explore in a future article, and that is in the absence of arming an artificially intelligent robot. We should all be fearful.
by David Waldron